Remote Server Access Made Easy - Intranet Penetration
Securely access your internal server from anywhere with FRP, a fast reverse proxy for remote intranet penetration.
Background
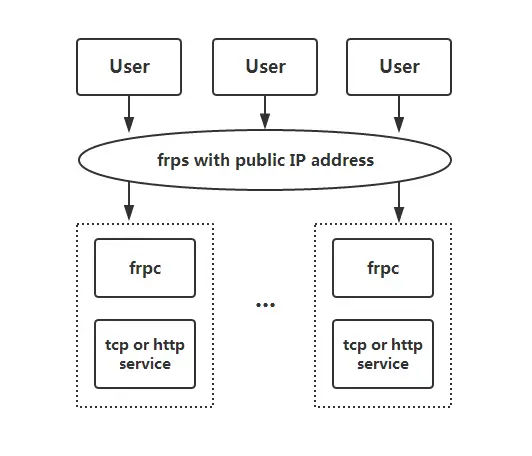
Intranet penetration (also called port mapping) is to map the local intranet port to the public network (also called the external network). The intranet is actually a local area network. If you want to access your company's internal network at home or in any public place, you need to penetrate the intranet. Project websites that can only be accessed on this machine can be accessed on other people's networks through intranet penetration.
FRP is a fast reverse proxy that allows you to expose a local server located behind a NAT or firewall to the Internet. It currently supports TCP and UDP, as well as HTTP and HTTPS protocols, enabling requests to be forwarded to internal services via domain name. FRP also offers a P2P connect mode.
Pre-requisites
- A server. In this article I will use the Linux server as an example.
- Server port 6000 open (this can be customized).
Deployment
- To begin, download the latest program for your operating system and architecture from the Release page. Take Linux version as an example (Please check latest version)
wget https://github.com/fatedier/frp/releases/download/v0.54.0/frp_0.54.0_linux_amd64.tar.gz
tar -xzvf frp_0.54.0_linux_amd64.tar.gz
-
Next, place the
frpsbinary and server configuration filefrps.tomlon Server A, which has a public IP address. -
Finally, place the
frpcbinary and client configuration filefrpc.tomlon Server B, which is located on a LAN that cannot be directly accessed from the public internet. -
Modify
frps.tomlon server A by setting thebindPortfor frp clients to connect to:
# frps.toml
bindPort = 7000
- Start frps on server A. (To have it run in the background, I’m using
nohup. You can also set it as a system service)
nohup ./frps -c ./frps.toml
- Modify
frpc.tomlon server B and set theserverAddrfield to the public IP address of your frps server:
# frpc.toml
serverAddr = "x.x.x.x"
serverPort = 7000
[[proxies]]
name = "ssh"
type = "tcp"
localIP = "127.0.0.1"
localPort = 22
remotePort = 6000
Note: The localPort (listened on the client) and remotePort (exposed on the server) are used for traffic going in and out of the frp system, while the serverPort is used for communication between frps and frpc.
- Start frpc on server B:
nohup ./frpc -c ./frpc.toml
Access Server on the Intranet via SSH
Important: To ensure security, I’ll disable password login and force keyfile login. You can reference my previous post:

Check your system configuration and firewall to allow remote access.
To access server B from another machine through server A via SSH (assuming the username is testuser), use the following command:
ssh -oPort=6000 -i /your/path/keyfile.pem [email protected]
Copyright statement: Unless otherwise stated, all articles on this blog adopt the CC BY-NC-SA 4.0 license agreement. For non-commercial reprints and citations, please indicate the author: Henry, and original article URL. For commercial reprints, please contact the author for authorization.

